Lessons Learned From The 2014 Blackhat Security Conference
The annual Las Vegas Blackhat security conference draws great attention from the media as the showpiece for trendy cyber security topics. From its inception in 1997, Blackhat has grown into a global conference series with additional stops in Abu Dhabi, Barcelona, and Washington DC. The conference includes the latest researchers from leading security companies such as Mandiant and McAfee. It also features the latest computer hacks and exploits for everything from commercial point of sale devices to mobile phones and broadband Internet modems.

University of Cambridge study showing overall credit card fraud did not drop after introduction of chip and pin security technology by MasterCard and Visa
While attending Blackhat this year, I discussed the latest credit card system exploits from security experts from the University of Cambridge, learned how the most dangerous viruses are designed to avoid detection from researchers at Intel Brazil, and discussed advancements in security risk management practices with employees of the Department of Homeland Security and the FBI.
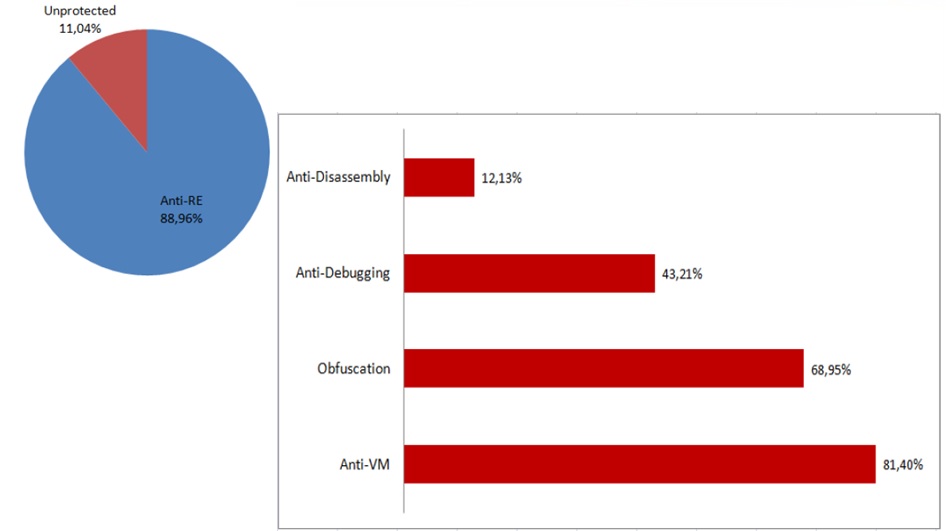
Research from Intel Brazil showing techniques hackers use 89% of the time to avoid detection by malware scanners
In addition to attending a diverse menu of security briefings, I participated in a two day boot camp covering new techniques in identifying and responding to network security threats. The security team at Mandiant has put together a free, open source collection of security tools available at no charge that rivals the best commercial incident response products on the market. The techniques and tools presented at Blackhat is truly state of the art and goes to show what a growing community of dedicated security professionals is capable of in responding to the current cyber security threat.
While the training was truly phenomenal, it was also quite terrifying. The hacker demonstrations at the conference showed that our information is not safe on the Internet. A great deal of work has to be done to combat the increasingly complex attacks against our information infrastructures. Attackers are out in front of the defenders in both sophistication of techniques employed and the ability adroitly apply a catalogue of various techniques in customized attacks that thwart the best of our digital defenses. This is a global information war that the West is quickly losing.
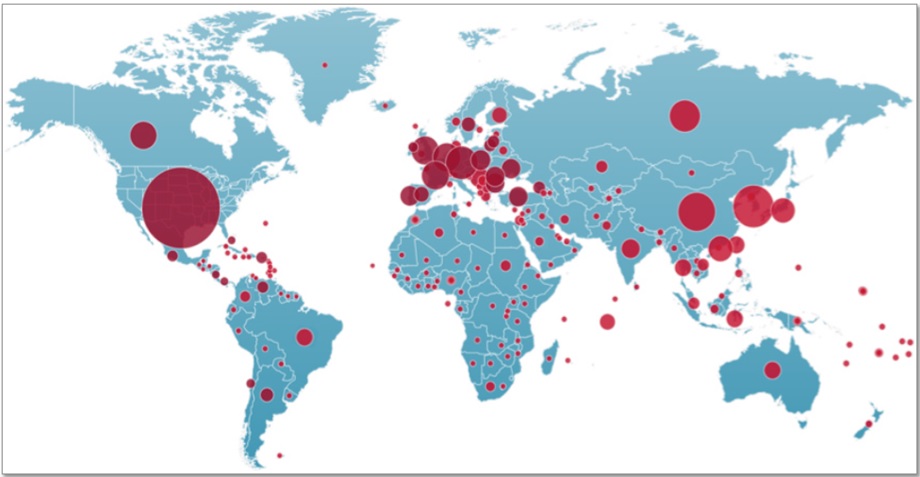
Briefing 'Leviathan' showing over 30 million instances of command and control botnet activity across the planet during 2013
According to former Defense Secretary Robert Gates, the Pentagon is “desperately short of people who have capabilities (defensive and offensive cyber-security war skills) in all the services and we have to address it."
Here are the main issues highlighted by the conference:
- Security planning is not thoroughly on most information systems by companies or the government. Without planning, mounting a defense is often futile against the current crop of hackers.
- Security spending needs to rise significantly if we are to offset the current growing losses due to cybercrime.
- Standards for online security need to be established that cover existing systems while including anticipated growth of leading technologies such as cloud and smart devices.
- Nation states are very actively involved in information spying and warfare. Companies and the state agencies must accept a much higher threshold of responsibility when securing consumer and business partner data because it is not just the computer geek down the street hacking into their systems anymore.
- The spread of data to mobile end user devices, such as smart phones and tablets, opens up a whole new exploitable surface for attackers.
Fortunately, every problem comes an opportunity for entrepreneurial product development and the subsequent investor that identifies these investment opportunities at early stages. I have stated many times that investing at the beginning of a bull market is the easiest way to long term wealth generation, whether that market be stocks and bonds, real estate investment trends, or precious metals. Here are the fundamentals underlying the security bull market.
- I believe the cyber security market is beginning the early stages of a mega-ramp where eventually a quarter-trillion dollars will be spent on product development and consulting services.
- Companies have to protect what they have to survive in the market, so security spending must increase to match the threat. The alternative is going out of business.
- Governments are in an online arms race similar to what we experienced during the nuclear build up during the cold war. Governments have certain security mandates and the state pocket books will open to accommodate those mandates.
- Security consulting is already booming. After completing my Masters in Security Assurance, my phone has been ringing off the hook with offers of new employment. Companies are spending big dollars on talent and the latest research shows that more students will enter information security as a career than ever before this year due to demand for security talent.
- Cyber security is a global market including less developed countries in Africa.
Computerworld predicts that security technology spending will go up 46% in 2015. For infrastructure, Computer world predicts that cloud computing will increase by 42% and data analytics dollars will improve by 36%. Mobile/wireless spending will increase 35%. Here is how to view these three infrastructure trends in relation to security spending.
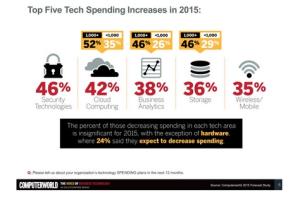
- Companies providing big data analytics platforms for analyzing massive security logs for attacks will be a particular area that investors will want to keep tabs on.
- Security remains one of the top concerns of companies considering the cloud. Because cloud usage is increasing, cloud security technologies must growth with it. In fact, government compliance standards like FISMA and FedRAMP requires prescriptive application of certain security controls. Enhancements in security appliances and services are needed for the government and all companies doing business with .gov. The very slow approval of FedFAMP status to cloud providers the last 2 years attests to the weakness of cloud security against the robust security controls template required by the US government.
- Mobile device security is a booming market as smart devices proliferate.
- Security consulting services have higher profit margins than product-oriented businesses and will see continued sales growth as long as cyber security remains a top concern of decision-makers.
I profile one company that addresses each of these concerns while growing by leaps and bounds.
Palo Alto Networks (PANW)
Palo Alto originally made a name for itself by challenging the existing stateful network packet firewall model with application firewalls that allowed security teams to address security at the user level in addition to the network packet level. Palo Alto has designed an integrated network security product that looks at the application traffic, compares it to a global database of malware called WildFire, and uses real time updates distributed globally to stop the spread of malware across subscriber's networks. This model works much more quickly than the stand alone Antivirus model employed by most security companies.
In the IT consumer era, companies that capitalize on securing user data traffic will grow while those that focus only at the network layer will fall behind. The end point, such as desktop computers, tablets, and smart phones, are increasingly the target of hackers looking for intellectual property and financial data. End points are easier to compromise due to 1) lack of security awareness of end users compared to systems security administrators and 2) the lack of end point application level security solutions present on most networks.
With the introduction of TAPS late this year, Palo Alto is challenging the traditional end point security model pioneered by Symantec, McAfee, and Kaspersky focused on malware signatures. With over 50 million new malware introduced every year, TAPS bypasses the signature-based model and addresses the threat by trapping those common malicious behaviors before they can do damage. TAPS provides preventative end point security whereas existing AV companies are left to address attacks only after they have done their damage.
Palo Alto works agnostically of network design and has strategic partnerships with Citrix (CTXS) and VMware (VMW) to support cloud networking. In addition, Palo Alto partners with Splunk (SPLK) for big data analytics across a company's broad systems infrastructure. Therefore, Palo Alto directly addresses three of our key security growth areas in cloud, mobile device, and security consulting. Palo Alto indirectly addresses big data analytics growth with the Splunk application partnership.
With over 21,000 customers, Palo Alto has a large existing addressable market of infrastructure customers to sell product additions to. In addition, the company obtains 47% of revenues from security services that include design and implementation of existing products as well as general security consulting. Security consulting is higher margin than equipment sales and support and should engender higher than average profit margins against companies that focus only on hardware and/or software offerings.
The company has excellent financials with current assets almost equal to total liabilities. Large borrowings in 2014 support the land grab model Palo Alto is using to capture market share against entrenched competitors in the AV and security device market. However, analysts are generally pleased with the approach as Palo Alto's integrated security solutions offer a market advantage against competitors with less integrated product offerings.
The stock is overvalued at over 20 times price to book based upon market expectations of future revenues. The current price has more than doubled this year and is unjustified, in my opinion, until Palo Alto reaches profitability. The tech sector, however, has seen much higher valuations before and it would not surprise me to see the stock price continue to rise in anticipation of handsome profits and expansive margins compared to the security technology market. This one is on the watch list, but I won't participate until the price comes down and the company begins to turn profits consistently. Once that happens, expect continued growth and solid financial performance from a true market upstart.
The author is not invested in any funds mentioned in the article.