Ransomware: Should WannaCry Make You Wanna Buy Cyber Equities?
Summary
- The WannaCry Ransomware Attack impacted over 200,000 users across 150 countries, but netted the hackers almost nothing (yet).
- Blame for the attack has shifted between Microsoft (MSFT) and the NSA (who both knew of the flaw), as well as the yet-to-be-identified attackers.
- We believe this attack is both unique and precedent-setting, and should be taken into account by investors when evaluating digital transformation initiatives and operational expenses of potential investments.
- We see short-term potential for selected cybersecurity equities.

On Friday, May 12, 2017, the world was hit with what I'll call the first "intelligently automated" ransomware attack, spanning over 150 countries and 200,000+ victims. That's pretty "global" if you consider there are only 196 countries in the world.
We covered the attack on the 15th of May, 2017, during the Cheddar Opening Bell session from the NYSE. You can watch the video here, and then dive into a bit more of the details below, including a list of the vendors and providers that may benefit from this attack through increased demand for software or security services.
Microsoft, the NSA, and the Shadow Brokers
On Friday, over 200,000 users found their computer systems locked (encrypted) by the WannaCry/WannaCrypt tool, and were presented with instructions to pay $300 in bitcoins if they ever wanted to see their data again.
As ransomware attacks go, this was fairly straightforward, followed a well-known process, asked for an accepted, and low, payment, and started with a user opening an email and falling victim to a phishing attack (see the attached graphic from Carbon Black).
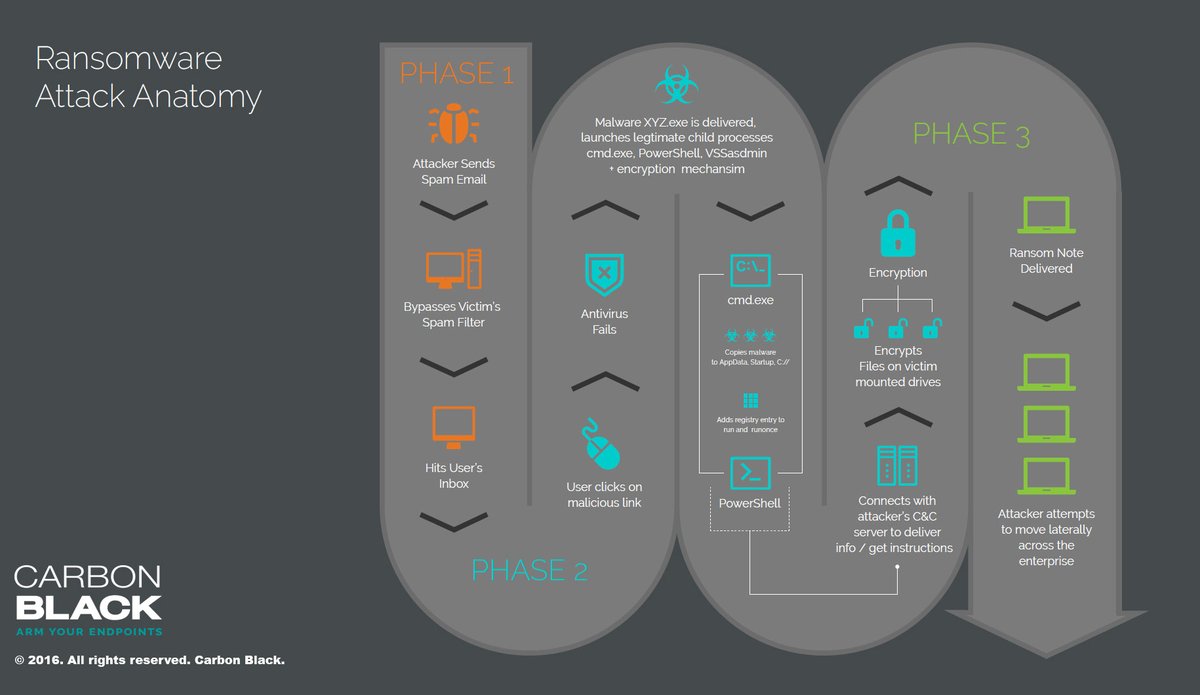
But, as ransomware attacks go, this one was also unique in several different ways, including its complexity, that begins in 2014 with Microsoft and the honorable pursuit of profits. Here's a breakdown of the timeline to provide some context around this event:
The Backstory
2014: Microsoft stops supporting Windows XP (and subsequently 8 and Server 2003) to cut costs and promote newer operating software. This includes security updates.
2016: NSA (allegedly) discovers a vulnerability in Windows products, related to the Microsoft SMB (Server Message Block) function. The vulnerability is "weaponized" through an exploit tool it creates called EternalBlue. At this point, numerous Microsoft operating systems are vulnerable.
2016: Shadow Brokers hacks NSA, acquiring NSA cyber tools, including EternalBlue.
February 2017: Microsoft unexpectedly delays its scheduled Patch Tuesday software update due to a "last minute issue".
March 2017: Microsoft releases the delayed software patch/update (which includes an un-sourced fix for the SMB vulnerability).
April 2017: Shadow Brokers dump NSA's EternalBlue SMB exploit onto the dark web (part of an ongoing 8-month-long dump).
April 2017: Microsoft confirms the SMB vulnerability targeted by EternalBlue has "already been fixed" for supported systems (primarily Windows 10, and excluding XP, 8, and Server 2003). Conspiracy theorists point to Microsoft's Patch Tuesday delay, wondering, at the time, "who tipped them off?"
The Attack
May 12, 2017 (Morning): WannaCry (WannaCrypt) appears, striking computers in Europe (Russia, Ukraine) before Asia (Taiwan), India, and North America (with little impact, as the US has a higher adoption rate of newer Windows operating software compared to other regions).
By melding EternalBlue software to ransomware software, allowing the attack to spread automatically without any human intervention, up to 300,000 machines are infected within 3 days. This is new to ransomware.
May 12, 2017 (Mid-day): Microsoft, realizing the scope of the attack, quickly pushes out a security patch (update) for Windows XP, 8, and Server 2003, attempting to get users (who may not be aware they are running old, vulnerable software) to quickly install the new software.
May 12, 2017 (Afternoon): A 22-yr old security researcher (under the Twitter handle @MalwareTech) working with security firm Proofpoint (Nasdaq:PFPT), realizes WannaCry is placing calls to a non-existent domain (iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com).
@MalwareTech registers the domain (for $10.69) as part of a routine bot-tracking effort. After the domain is activated, the WannaCry software, now able to reach the specified domain, turns dormant and stops spreading.
The domain that was being pinged by WannaCry was a "kill switch" of sorts, designed to either halt the attack (if the domain were registered by the attackers) or prevent the code from being researched by security teams (in a virtual environment). While the attack is stalled, it does not, however, unlock any encrypted files.
May 14, 2017: Updated versions of the WannaCry software begin to appear, without the kill switch, but have limited success.
The Aftermath
May 14, 2017: Microsoft strongly hints the US Government (e.g., NSA) is at fault for enabling the attack and suggests the creation of a Digital Geneva Convention to "commit governments to protecting civilians from nation-state attacks in times of peace" (there's no mention of what happens when the cyber gloves are off).
May 15, 2017: Researchers uncover clues that MAY (or MAY NOT) link the WannaCry attack to a group of hackers allegedly tied to North Korea (note: the Shadow Brokers group has hinted it will release data from SWIFT network users, as well as nuclear secrets of Russian, North Korean, and Chinese governments).
May 15, 2017: Researchers track ransom payments (in relatively untraceable bitcoins) of over $50,000 to three different accounts. However, in an unusual move, suggesting money may not have been the motive of the attack, the money has not been touched.
May 16, 2017: Shadow Brokers threatens additional releases of NSA-sourced cyber tools.
Unpacking the Hack
Breaking this attack down, it starts like almost every other ransomware attack: a phishing email that fools a user into clicking a "link", giving the hacker access to the user's computer, which it then encrypts, Ransom is occasionally (and unwisely) paid. And, usually, it ends there.
Ransomware targets are generally not targeted for specific reasons, and in fact casting a wide net to ensnare a larger number of unsuspecting, and cyber-challenged, users seems to be the most effective approach for most ransomware hackers.
The WannaCry attack was different in that it utilized a tool (EternalBlue) that allowed the software to operate autonomously after infecting the first computer, enabling it to actively look for, and leverage, the SMB vulnerability to spread laterally throughout an organization.
While most ransomware attacks target single computers (or file structures), WannaCry acts much like more traditional viruses or malware, and is capable of spreading throughout an organization, magnifying the impact.
The concern now is that the level of threat will grow with the next wave, as cyber attackers learn from this approach and find creative ways to exploit the NSA tool-kit. Reports have already emerged that another hacker group has exploited the same Microsoft vulnerability (and NSA code) to attack, and leverage, over 200,000 machines in the production of fake digital currency (estimated haul of over $1m to date).
Where's the Blame?
Microsoft has been blunt in its criticism of the NSA, while others are now discussing the lack of responsibility on the part of Microsoft for not offering ongoing security updates. This is key as we now know:
The NSA did, in fact, alert Microsoft earlier this year that its EternalBlue code had been stolen, and Microsoft prepared but did not release the XP patches back in February!
If there's a hero here, it isn't Microsoft.
To be fair, enterprises could have played a role in stopping this attack (and many did), by increasing cybersecurity awareness and education of employees, and ensuring that corporate computer systems are both running newer versions of software AND utilizing off-the-shelf anti-malware tools. But that costs money.
Far too many IT departments have learned to push older, and increasingly vulnerable, technology to the back office and extend the life of both hardware and software far beyond expected uses. This presents an ongoing risk to a firm's management, to its users/customers, and to its investors.
The risk, as many are now learning, can be significant, and we encourage more Boards and investors to start asking more pointed questions. Expect this to come up during an earnings call whenever management - in any sector - discusses increased/decreased IT or digital operational spend.
Remember, if the NSA had not tipped off Microsoft back in February, Windows devices would still be at risk today (a significant issue given the hyper-connected nature of our economy and the over-reliance on Windows operating software).
Where's the Benefit?
Clearly not to the attackers, at least from a financial perspective. The attackers have only been successful in garnishing just over $50,000 (split between three different accounts, oddly). If the average person paid the up-front $300 ransom in bitcoins, that works out to about 170 payments, from over 200,000 machines held hostage - not a great ROI.
It appears that the most immediate beneficiaries of this attack are the providers of cybersecurity products and services, whether or not they relate to preventing this particular type of attack.
We've long held that cybersecurity spend is event-driven in the short term, though CFOs can be prone to memory loss after a few months or even weeks following "the event". Once a wave has begun, chances are pretty good that we can predict how many quarters (if not months) it will be before revenue from new sales returns to normal growth rates. For that reason, we try to focus, not on the impact of a specific event - although all major cyber security events should be examined for patterns and trends - but the where vulnerabilities lie.
Vulnerabilities, assuming they are both major and difficult to find (as most are), will eventually be exploited. The ongoing release of NSA exploit tools is likely to increase risk (it's unclear if the NSA's heads-up policy towards Microsoft applies to other exploits, or other vendors).
The issue, for both users and enterprises, will continue to be of concern. For example, we believe that, as wireless devices (primarily smartphones) increasingly become a primary conduit to access enterprise applications and important data, they continue to represent a critical and vulnerable backdoor.
Increasing spending to bolstering the defense of that backdoor is one of the key pillars underlying our investment in Blackberry (Nasdaq:BBRY), which has now made the transition to a software company with almost no exposure to devices and hardware (although, its valuation would suggest that at least some institutional investors continue to see the company that way).
Another example are threats that involve insiders and/or unauthorized (but normal looking) access, deletion, and/or exfiltration of data that, from a network perspective, would not appear anomalous. We believe that the software tools from market-leading data protection and access auditing software company, Imperva (NYSE:IMPV) will be increasingly in demand do to this emerging set of vulnerabilities.
We've compiled a list of players, broken down by hardware/software vendors and security service providers and sorted by gains between closing on 11 May 2017 (the day before the attack hit) and closing on 16 May 2017.
| Selected Cybersecurity Vendors | Close 11 May 2017 |
Close 16 May 2017 |
|
| Sophos (SOPH.L) in GBp | £338.80 | £369.80 | 9.15% |
| Barracuda Networks (NYSE:CUDA) | $21.14 | $23.00 | 8.80% |
| Blackberry | $9.38 | $10.18 | 8.53% |
| FireEye (Nasdaq:FEYE) | $14.45 | $15.65 | 8.30% |
| Mimecast (Nasdaq:MIME) | $24.88 | $26.26 | 5.55% |
| Fortinet (Nasdaq:FTNT) | $39.03 | $40.97 | 4.97% |
| Imperva | $47.45 | $49.10 | 3.48% |
| Palo Alto Networks (NYSE:PANW) | $115.15 | $118.67 | 3.06% |
| Proofpoint | $115.15 | $118.67 | 3.06% |
| Cisco (Nasdaq:CSCO) | $33.63 | $34.30 | 1.99% |
| Symantec (Nasdaq:SYMC) | $31.46 | $31.32 | (0.45%) |
| CyberArk Software (Nasdaq:CYBR) | $55.15 | $48.39 | (12.26%) |
Separate from vendors that focus on hardware and software products as primary revenue streams, with services as a secondary revenue stream, providers of managed security services and consulting work (which includes operational monitoring of security systems, identity management, intrusion detection, incident response, and security education) are primarily driven by services revenue (and often resell or manage the hardware/software of multiple hardware/software vendors).
| Selected Cybersecurity Providers | Close 11 May 2017 |
Close 16 May 2017 |
|
| Root9B (Nasdaq:RTNB) | $6.66 | $8.01 | 20.27% |
| SecureWorks (Nasdaq:SCWX) | $9.55 | $10.27 | 7.54% |
| Tata Consultancy Services* (TCS.NS) in INR | ₹2,349.45 | ₹2,429.15 | 3.39% |
| Wipro Limited* (NYSE:WIT) | $10.11 | $10.44 | 3.26% |
| Tech Mahindra* (TECHM.NS) in INR | ₹434.75 | ₹443.75 | 2.07% |
| IBM Security* (NYSE:IBM) | $150.65 | $153.68 | 2.01% |
| Accenture Security* (NYSE:ACN) | $120.80 | $123.14 | 1.94% |
| Cognizant Technology* (Nasdaq:CTSH) | $64.25 | $65.19 | 1.46% |
| Rapid7 (Nasdaq:RPD) | $18.34 | $18.59 | 1.36% |
| BAE Systems* (BA.L) in GBp | £641.00 | £643.00 | 0.31% |
| Infosys* (Nasdaq:INFY) | $15.27 | $15.26 | (0.07%) |
| Unisys* (NYSE:UIS) | $12.35 | $12.30 | (0.40%) |
*Note some of the providers listed above offer a much broader range of services than cybersecurity, ranging from IoT and mobile applications development to digital transformation and intelligent automation (as well as traditional business process outsourcing). However, security services do play a significant role in the ability to offer other digital/business service offerings and are commonly leveraged between internal and external requirements.
For more insights, check out this free trial of Samadhi's Perspectives on Tech offering in the ...
more